Resource Library
BROWSE OUR RESOURCE LIBRARY TO LEARN MORE ABOUT OUR
CAPABILITIES, SOLUTIONS, AND THOUGHT LEADERSHIP
CAPABILITIES, SOLUTIONS, AND THOUGHT LEADERSHIP

CAPABILITIES STATEMENT
Learn how Intelligent Waves collaborates, innovates, and integrates technologies to enable operational agility for resilient and secure communications.

CYBERSECURITY CAPABILITIES
Cybersecurity threats take many forms–terrorists, enemy states, rogue actors, and employees. Staying ahead requires an in-depth understanding of evolving technologies, constant vigilance, continuous monitoring, and comprehensive response. Intelligent Waves has provided end-to-end IT and cybersecurity solutions to the Federal Government since 2006 and understands that cybersecurity is more than IT security, vulnerability assessments, and threat mitigation; it is a business concern that requires a persistent effort and culture to align people, processes, and technology.
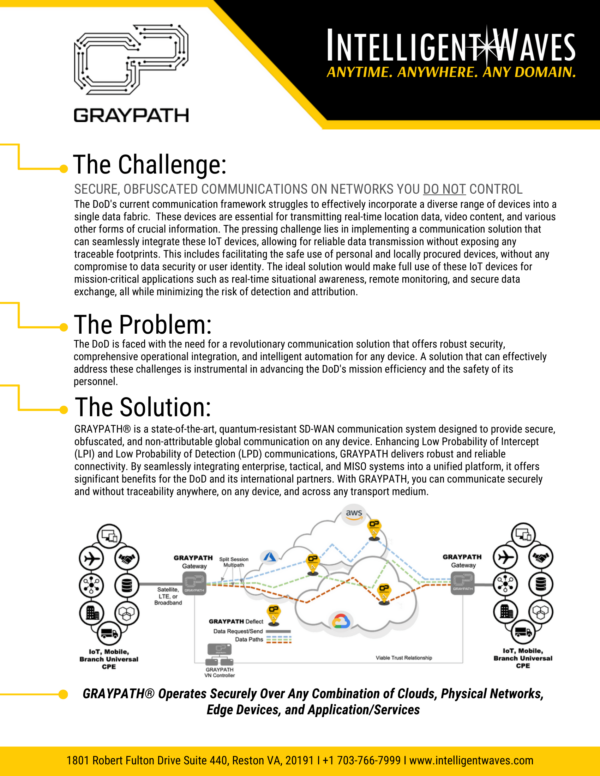
WHAT IS GRAYPATH?
GRAYPATH is a virtual networking approach comprised of software components that channelize, route, and accelerate application data to significantly enhance network security, reliability, and performance across branches and devices including laptops, tablets, phones, and IoT.
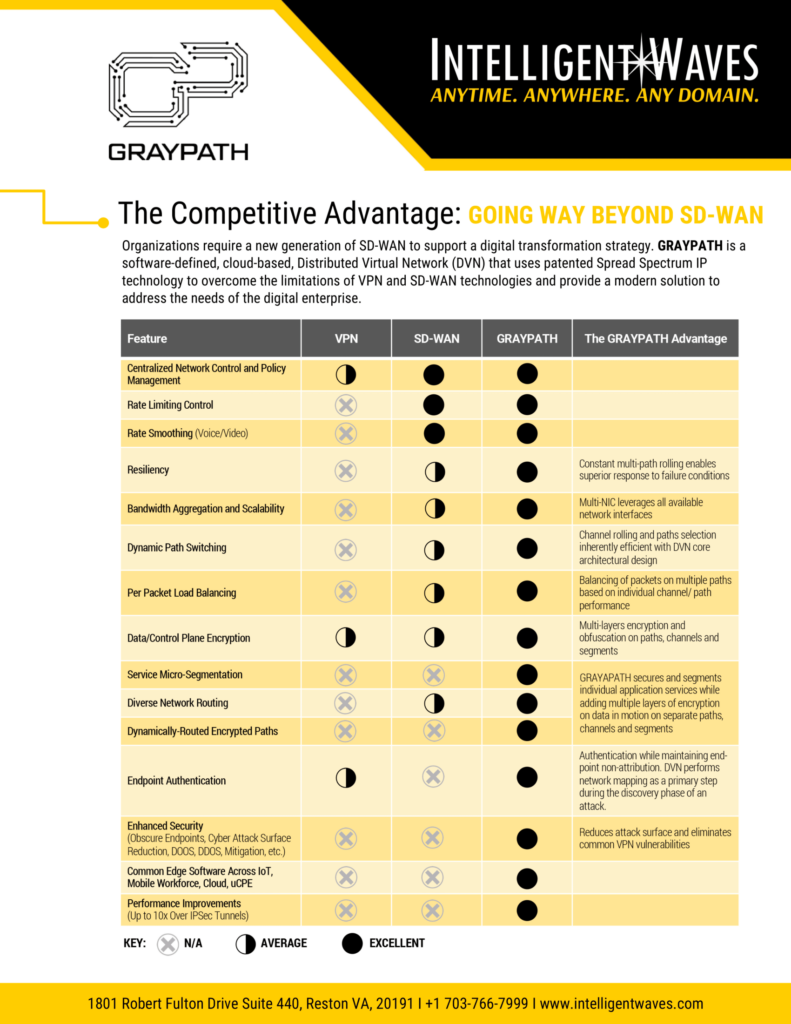
GRAYPATH COMPARISON
Organizations require a new generation of SD-WAN to support a digital transformation strategy. GRAYPATH is a software-defined, cloud-based, Distributed Virtual Network (DVN) that uses patented Spread Spectrum IP technology to overcome the limitations of VPN and SD-WAN technologies and provide a modern solution to address the needs of the digital enterprise.

PHANTOM SOLUTION BRIEF
Phantom Next Generation provides the ability for organizations to access foreign points of presence to conduct remote open-source information gathering and research while at the same time protecting organizations and individuals from exposure to foreign intelligence. Intelligent Waves has achieved this by combining the GRAYPATH software-defined obfuscated network with the managed attribution capability of the Phantom platform in a secure but unclassified package.

LiFi SOLUTION BRIEF
LiFi is a wireless connectivity solution for the near-peer fight that uses visible and infrared light to pass data through the open air. LiFi brings secure, field-expedient, wireless communications to any space regardless of data classification and sensitivity. Offering Low Probability of Intercept (LPI) and Low Probability of Detect (LPD) transmissions.
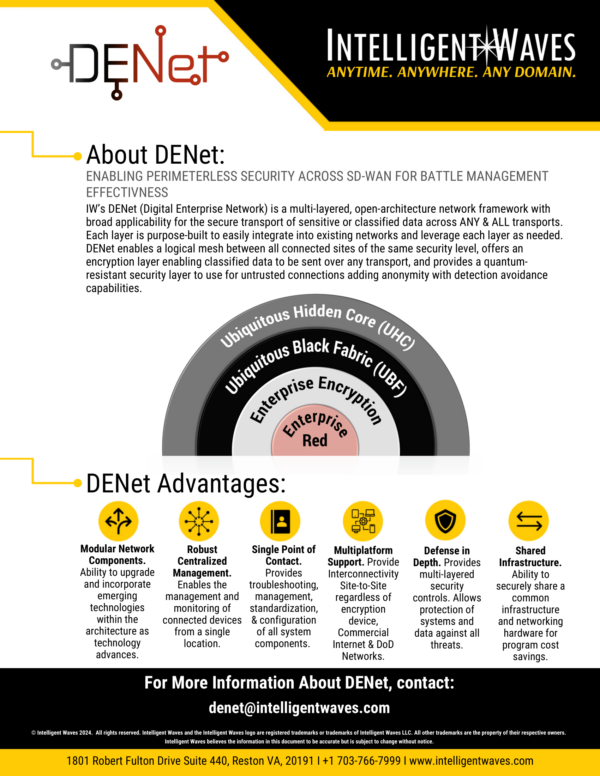
DENet SOLUTION BRIEF
DENet is a multi-layered, open-architecture network framework with broad applicability for the secure transport of sensitive or classified data across ANY & ALL transports. Each layer is purpose-built to easily integrate into existing networks and leverage each layer as needed. DENet enables a logical mesh between all connected sites of the same security level, offers an encryption layer enabling classified data to be sent over any transport, and provides a quantum-resistant security layer to use for untrusted connections adding anonymity with detection avoidance capabilities.

ENHANCE HUMAN PERFORMANCE BRIEF
IW’s ENHANCE is a proven next-generation Human Performance Solution that utilizes 360 degrees of strategic neurofeedback to enhance your pilots’ cognitive performance and resilience. Through objective metrics and tracking of cognitive states, ENHANCE empowers pilots to self-regulate, maximize their performance, and dramatically improve mental acuity for peak pilot performance.
BRAIN WAVES, INNOVATIVE THOUGHTS BY IW’S TECHNOLOGY EXPERTS

DOMINATING THE ELECTROMAGNETIC
SPECTRUM WITH LIFI IN SUPPORT OF THE
NEXT-GEN WARFIGHTER
The Electromagnetic (EM) War is On: Radio Frequency (RF) Communications is No Longer Sufficient
FSO and LiFi significantly increase the warfighter’s safety and capabilities and keep Commanders informed to accomplish the mission. Both FSO and LiFi are unsusceptible to data interception, jamming, and detection, while still providing superb data rate communications across the battlefield.

THE DATA DREAM TEAM:
Enhancing Organizational Value
to Achieve Mission Success.
Organizations continuously seek new ways to automate and accelerate their ability to make better-informed decisions driven by quality data. As a result, information creation and the associated ability to process data grow exponentially. As a result, organizations can no longer afford to see data as a byproduct and must value it as an organizational asset. To maximize the robust power of data, dedicating organizational resources throughout the operational life cycle will be more vital than ever. But where should those resources be allocated, and who in the organization is positioned to make the most of them?

PROTECTING THE KEYS TO THE CASTLE:
Relying on Technology is Not Enough. Organizations Must Have ICAM Policies in Place, Be Disciplined Enough to Follow
Them, & Diligent in Auditing Them to Ensure They Are Working
ICAM is the set of policies that an organization enforces via Information Technology (IT) systems to ensure the correct user or service is accessing the right information at the right time and via the right channel. This process is accomplished by focusing on reducing complexity for the user while increasing account and credential management via automation, monitoring, or centralizing services across its three main areas. These areas are Identity Management, Credentials Management, and Access Management. All three areas are equally important and require the same level of implementation prioritization to protect the sensitive information that is being guarded.

GRAYPATH
Adaptation or Extinction in the Digital Age
This white paper compares the GRAYPATH solution to legacy VPN and SD-WAN technologies. It explains why GRAYPATH is the superior technology to support digital transformation by providing secure, robust, and reliable connectivity to meet the needs of the digital enterprise.

ZERO TRUST ARCHITECTURE
An imperative Culture Shift to Proactively Protect Your Critical Assets
The key to successful implementation is understanding what you want to protect, where your risks lie and working with a knowledgeable partner to achieve your goals. Building a Zero Trust network does not need to be an all or none proposition. Start small and iterate as needed.