“The revolution in information technology, commerce, and politics since the Cold War’s end is only making open sources more accessible, ubiquitous, and valuable. Simply put, one can gather more open intelligence with greater ease and at less cost than ever before.”
– Stephen Mercado, Author of Sailing the Sea of OSINT in the Information Age
The Challenge:
Current communication systems within the DoD fail to adequately disassociate communicating parties and erase any traceable digital evidence. While some aspects of secure communication are addressed, the inability to fully break the digital trail exposes the identity of the individuals involved and jeopardizes the mission. Furthermore, existing systems lack built-in zero-trust principles, leaving them vulnerable to various attacks, particularly man-in-the-middle attacks. Moreover, the conspicuous nature of these systems and their susceptibility to insider threats put the mission and individuals at risk.
The Problem:
When operating in hostile environments, Warfighters face the challenge of communicating while maintaining their anonymity and operational security. Conventional approaches to secure data communications can inadvertently reveal identities, jeopardizing both individual safety and mission success. Such breaches can significantly impede decision-making superiority, potentially undermining strategic outcomes and operational efficiency.
The Solution:
REMOTE, SECURE, OBFUSCATED, MANAGED ATTRIBUTION
Addressing the critical gaps in secure communication within the DoD, Intelligent Waves presents a trio of robust solutions:

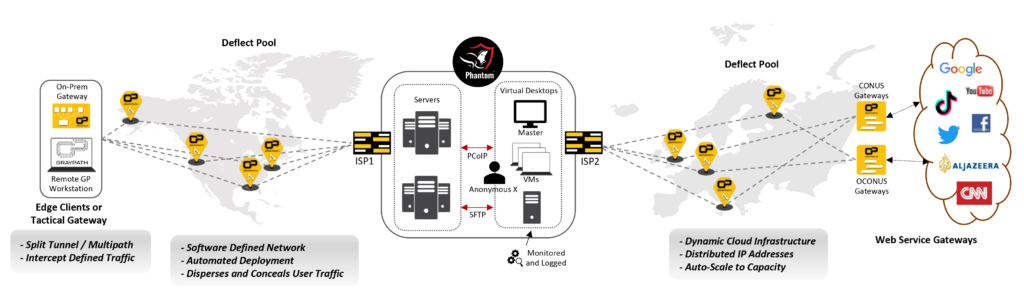
Phantom Desktop is a customizable cloud sandbox Virtual Desktop Infrastructure (VDI) that provides personnel with secure access to Open Source Intelligence (OSINT) sources from any location. This ground-breaking tool allows intelligence gathering without a physical presence in the area of interest, effectively reducing the risk of exposure and ensuring anonymity. Research, analysis, and data collection activities can now be conducted in a secure environment, without leaving a traceable digital trail.

For secure and non-attributable multi-factor authentication (MFA) essential in Military Information Support Operations (MISO), Phantom SMS comes into play. This web-based text messaging platform ensures that analysts can authenticate their access to various internet platforms without compromising heir security or revealing their identity, successfully eliminating the vulnerability of the mission and individuals.

In hostile environments, personnel need a solution that separates their physical presence from their electronic footprint. Phantom Mobile serves this purpose by facilitating obfuscated communications and forward-projected cellular presence through the Hypori Virtual Device framework. This allows analysts to operate on virtual Android phones securely, ensuring their physical location and identity remain disassociated from their electronic activity.
Phantom Next Generation Advantages:
The Phantom Suite provides the Warfighter with:
- Secure operation across networks, protecting mission integrity.
- Obfuscated data communication, maintaining stealth in all activities.
- The suite ensures a secure boundary between local private networks and remote public internet services.
- Enables misattribution.
- The tools are highly customizable and scalable, allowing them to adapt to various operational needs and serve a broad range of military applications.
Phantom Architecture: