Resource Library
Browse our resource library to learn more about our capabilities, solutions, and thought leadership
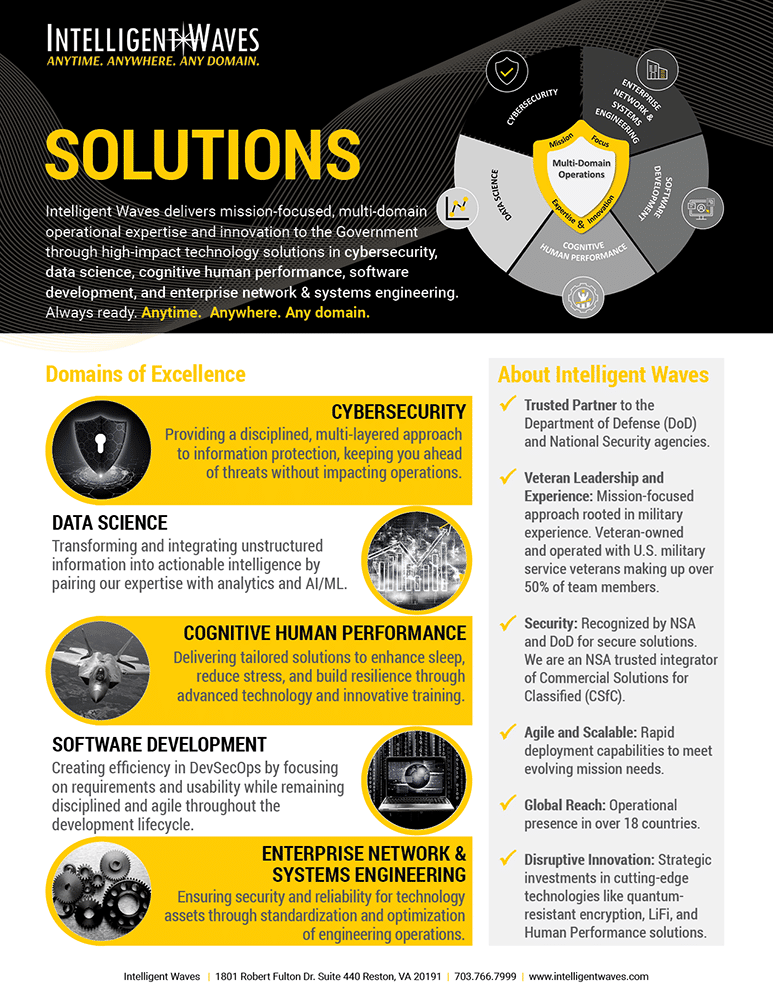
Solutions
Discover how Intelligent Waves drives mission success by combining operational expertise with cutting-edge technology to deliver resilient, secure, and high-impact solutions.

Innovations
Read about our mission-focused technology innovations in cybersecurity, data science, cognitive human performance, software development and enterprise network & systems engineering.

Cybersecurity capabilities
As a trusted cybersecurity expert to the Department of Defense (DoD) and other National Security agencies, Intelligent Waves is committed to delivering next-generation solutions that redefine how the defense community secures its operations.
By integrating artificial intelligence, zero-trust frameworks, and real-time operational capabilities, Intelligent Waves equips the defense community with tools to anticipate threats, adapt to dynamic operational requirements, and ensure uninterrupted mission success.
GRAYPATH®
GRAYPATH® is a turnkey, commercial off-the-shelf solution that ensures network survivability and traffic anonymity. Designed for versatile integration, GRAYPATH enables Low Probability of Intercept (LPI)/Low probability of Detection (LPD) operations to meet the demands of modern, mission-critical environments.
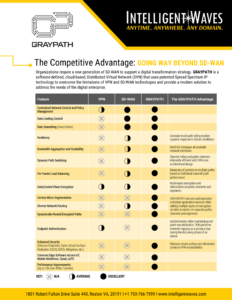
GRAYPATH® comparison
To drive digital transformation, today’s organizations need a next-generation SD-WAN solution. GRAYPATH® delivers just that – a turnkey, commercial off-the-shelf platform powered by patented Spread Spectrum IP technology. It resolves the limitations of traditional VPN and legacy SD-WAN systems, offering a modern, resilient solution tailored to the demands of the digital enterprise.
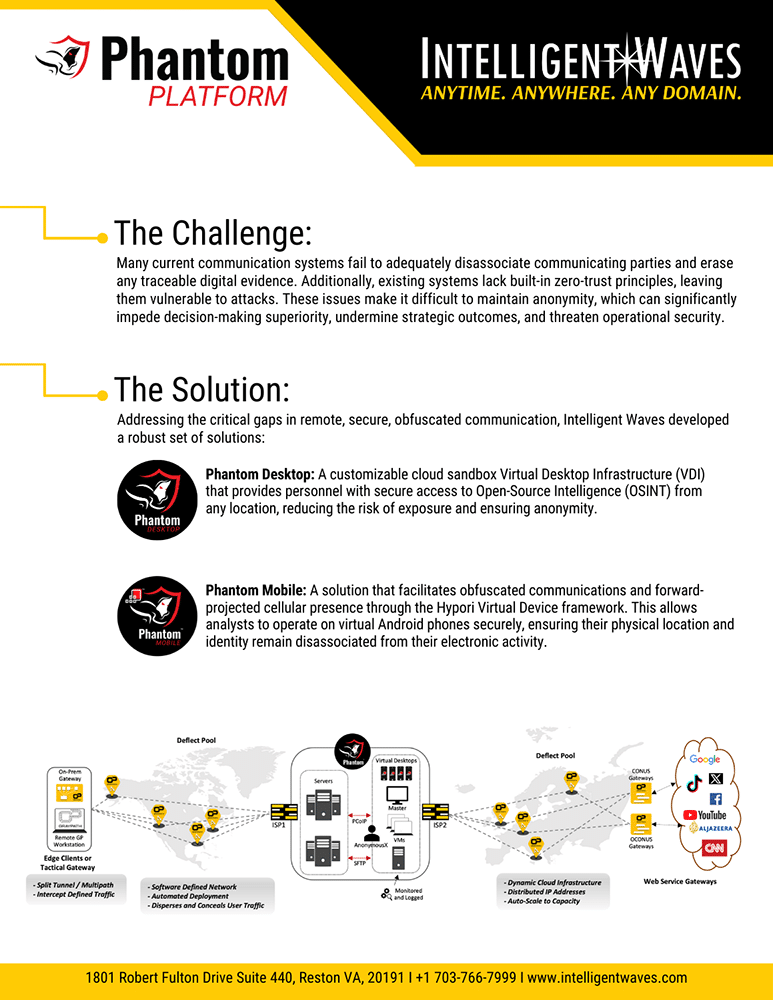
Phantom Platform
The Phantom Platform is a customizable, virtual solution that provides anonymous remote access for intelligence professionals. It ensures appropriate attribution, allowing users to tailor their digital persona while maintaining operational security.
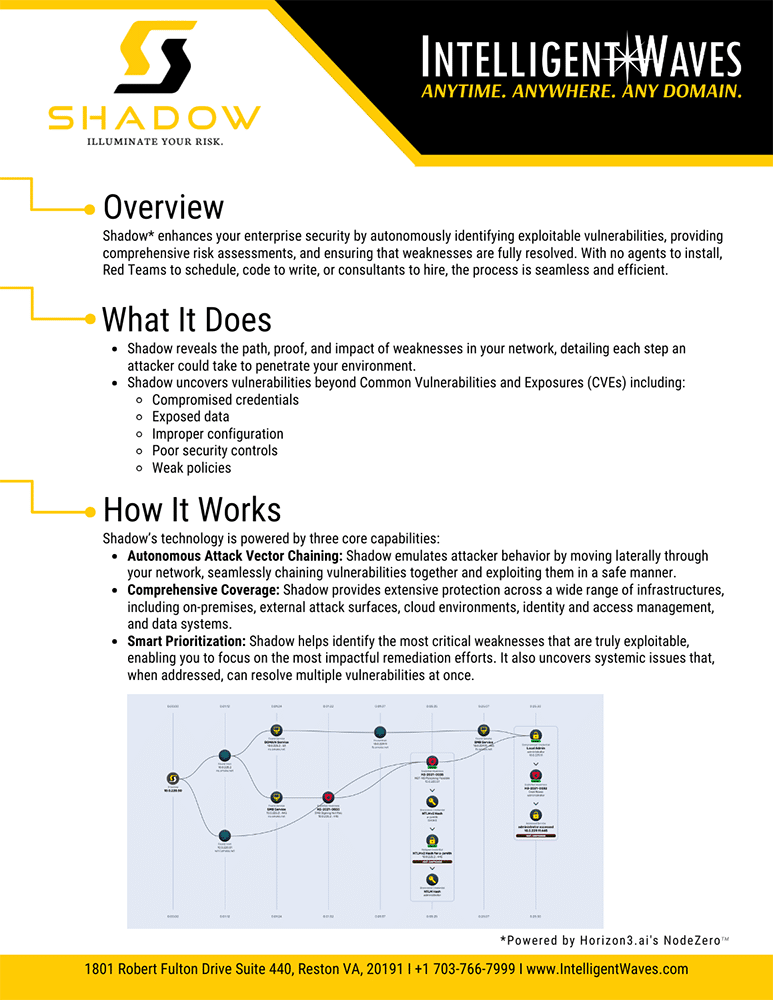
SHADOW
SHADOW is an autonomous solution that enables organizations to quickly prioritize exploits, continuously discover vulnerabilities, and verify compliance in real-time. Designed to secure critical data, it delivers fast, automated assessments to stay ahead of evolving threats.

LiFi solution brief
LiFi is a wireless connectivity technology that uses visible and infrared light to securely transmit data through open air. Ideal for the near-peer conflict, it delivers Low Probability of Intercept (LPI) and Low Probability of Detection (LPD) communications, with signals confined to physical spaces – meeting SCIF standards and supporting multiple security classifications.

DENet™ solution brief
DENet™ is a multi-layered, open-architecture network framework designed for secure transport of sensitive or classified data over any medium. Its modular layers integrate seamlessly with existing networks, forming logical meshes between sites of the same classification. DENet includes encryption for secure data transfer across any transport and a quantum-resistant layer for anonymous, detection-resistant communication over untrusted connections.
BRAIN WAVES, INNOVATIVE THOUGHTS BY IW’S TECHNOLOGY EXPERTS

DOMINATING THE ELECTROMAGNETIC
SPECTRUM WITH LIFI IN SUPPORT OF THE
NEXT-GEN WARFIGHTER
The Electromagnetic (EM) War is On: Radio Frequency (RF) Communications is No Longer Sufficient
FSO and LiFi significantly increase the warfighter’s safety and capabilities and keep Commanders informed to accomplish the mission. Both FSO and LiFi are unsusceptible to data interception, jamming, and detection, while still providing superb data rate communications across the battlefield.

THE DATA DREAM TEAM:
Enhancing Organizational Value
to Achieve Mission Success.
Organizations continuously seek new ways to automate and accelerate their ability to make better-informed decisions driven by quality data. As a result, information creation and the associated ability to process data grow exponentially. As a result, organizations can no longer afford to see data as a byproduct and must value it as an organizational asset. To maximize the robust power of data, dedicating organizational resources throughout the operational life cycle will be more vital than ever. But where should those resources be allocated, and who in the organization is positioned to make the most of them?

PROTECTING THE KEYS TO THE CASTLE:
Relying on Technology is Not Enough. Organizations Must Have ICAM Policies in Place, Be Disciplined Enough to Follow
Them, & Diligent in Auditing Them to Ensure They Are Working
ICAM is the set of policies that an organization enforces via Information Technology (IT) systems to ensure the correct user or service is accessing the right information at the right time and via the right channel. This process is accomplished by focusing on reducing complexity for the user while increasing account and credential management via automation, monitoring, or centralizing services across its three main areas. These areas are Identity Management, Credentials Management, and Access Management. All three areas are equally important and require the same level of implementation prioritization to protect the sensitive information that is being guarded.

GRAYPATH
Adaptation or Extinction in the Digital Age
This white paper compares the GRAYPATH solution to legacy VPN and SD-WAN technologies. It explains why GRAYPATH is the superior technology to support digital transformation by providing secure, robust, and reliable connectivity to meet the needs of the digital enterprise.

ZERO TRUST ARCHITECTURE
An imperative Culture Shift to Proactively Protect Your Critical Assets
The key to successful implementation is understanding what you want to protect, where your risks lie and working with a knowledgeable partner to achieve your goals. Building a Zero Trust network does not need to be an all or none proposition. Start small and iterate as needed.
